How Secure Is Your Company Video Surveillance Equipment?
Like other IoT devices, video surveillance equipment may be prone to privacy breaches. Learn how to secure your company’s video surveillance equipment.

According to a survey conducted by the IHS Markit Video Surveillance Group, some 98 million network surveillance cameras were shipped in 2017 along with almost 30 million HD CCTV (high-definition closed-circuit television) cameras. These impressive numbers are likely no surprise: Video surveillance equipment is everywhere. In parking lots, hospitals, shopping malls, local businesses such as banks and more. Video equipment is something that enterprises rely on for safety measures and for business analytics.
But many stakeholders don’t realize that surveillance equipment can be an extremely vulnerable entry point for data-breaches and hacks. Imagine this scenario. A business with a chain of retail stores installs small network-connected video monitoring cameras at each retail location in order to prevent shoplifting, monitor retail employers who deliver cash deposits to banks and also to secure valuable business analytics such as volume of shoppers and average time spent in front of each merchandising display. A perpetrator finds a way to penetrate the network and assumes immediate control of the live stream and data traffic is then routed to an adversary in a country such as China. This is how IP and business intelligence ends up in the wrong hands.
This type of breach is occurring with increased frequency. So how do businesses maintain their safety and asset-protection measures while ensuring their video surveillance equipment remains secure? The challenge of securing video surveillance equipment is multifold. In order to secure surveillance equipment, you need to find a way to secure both the actual video camera and the network. In addition, due to practicality, the security measures generally must be put in place remotely.
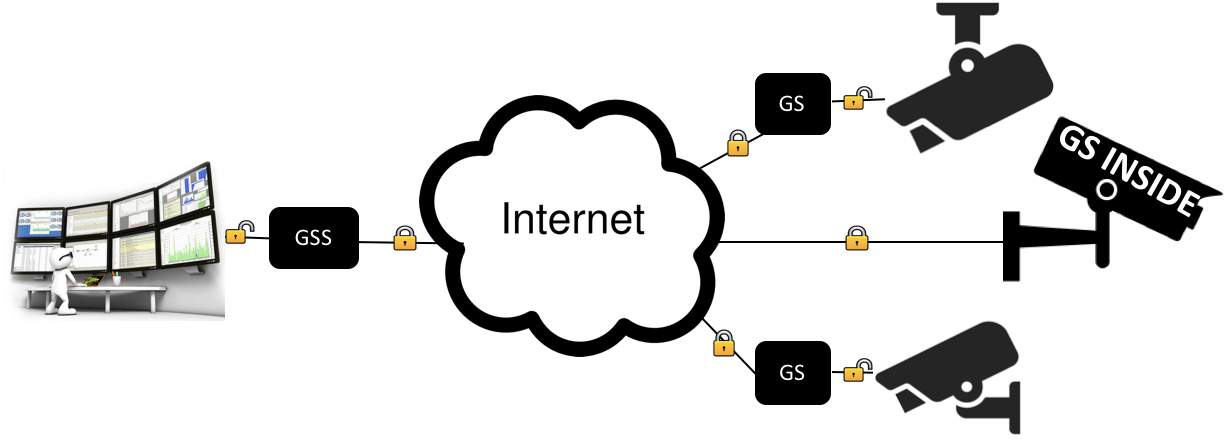
The solution becomes finding a way to tighten the security of the cameras live streams via the network while introducing potential new methods of securing the video equipment itself. GoSilent (labeled GS in the below diagram) plugs directly into the individual video cameras and secures a connection to the enterprise GoSilent server (labeled GSS in the below diagram), and creates an Internet protocol security (IPsec) tunnel through the enterprise firewall. The camera live streams are then securely transmitted, viewed and stored behind the corporate firewall without risk of interception.
Learn more about how Silent Circle’s products and solutions help enterprises secure their data and prevent losses in reputation, trust and earnings.