Law Firms Must Close The Gap On Cybersecurity Risk
The legal industry has been increasingly under attack from cyberthreats. Learn more about these cyber attacks and how they can be stopped.

According to the American Bar Association’s (ABA) 2017 Legal Technology Survey Report, 22% of respondents indicated that their law firms had suffered a data breach at some time - up from 14% in the prior year. This comes as no surprise given the access that attorneys have to a very wide range of sensitive client information. The cyberdefense of many law firms is far less robust than that of their clients, making the firms attractive targets for cybercriminals seeking access to private data. As far back as May 2014, the New York Ethics Opinion 1019 warned attorneys about this threat environment:
“Cyber-security issues have continued to be a major concern for lawyers, as cyber-criminals have begun to target lawyers to access client information, including trade secrets, business plans and personal data. Lawyers can no longer assume that their document systems are of no interest to cyber-crooks.”
Real Damage
Numerous high profile incidents involving data compromise have occured at law firms due to inadequate digital security measures. For example, the hacking of international law firms has resulted in the exposure of non-public information used for insider stock trading. Meanwhile, some law firms have been forced to temporarily shut down phone, email and information systems due to a cyber attack.
Attorneys appear to be behind the curve when it comes to protecting digital assets. The above referenced ABA report revealed that many law firms do not use digital security measures considered to be basic by security experts. Furthermore, when compared to other businesses and professionals, the legal profession consistently falls behind when it comes to cyber protection. It appears that criminals are well aware of this gap as the rate of attacks on law firms has been steadily increasing.
Critical Issue
The attorney-client relationship thrives only as long as confidentiality and trust remain intact. This places the lawyer’s responsibility to protect client information at a level perhaps even higher than the client’s own. The reality is that attorney cyber-security negligence is indefensible in the digital age.
In order to improve protection, one of the most important steps is to incorporate digital security into the culture of an organization. The threat and potential damage caused by hackers make cyber defense much more than just an “IT problem”. From staff training to executive buy-in, security issues lie at the core of a law firm’s integrity and survival.
Real Solutions
In order to keep networks and data safe, some law firms have set-up an enterprise security program (ESP). Carnegie Mellon University’s Software Engineering Institute has established a list of recommended activities for establishing and maintaining a basic ESP:
- Establish a cross-organizational security team comprised of practice chairs and representatives from each department, including procurement (they purchase office equipment that has servers) and meet quarterly.
- Create and communicate policies regarding the privacy and security of firm data. This includes the use of encryption, remote access, mobile devices, external drives, laptops, WiFi hotspots, clouds, email accounts and social networking sites.
- Inventory the firm’s software systems and data, assign ownership and categorize by risk level. Extremely sensitive matters that have the highest risk may need stronger security protections and stronger access controls.
- For each office (including foreign offices), identify points of contact with law enforcement, ISPs, communications companies that service the firm and cybersecurity experts.
- Conduct third-party vulnerability scans, penetration tests and malware scans. Do not rely on antivirus software.
- Perform software code reviews on all web-based applications and custom code to detect any vulnerabilities.
- Develop a 2-5 year security strategic plan and 12-month security activity program plan.
- Deploy robust security technologies for encryption, intrusion prevention and detection, monitoring and security event management.
- Identify and document security controls.
- Establish security configuration settings, access controls and logging.
- Develop security policies and procedures to support the security plan and technologies.
- Conduct training on information security awareness, protocols and governance.
- Develop and test incident response, business continuity or disaster recovery plans and communications plans.
- Develop contractual security requirements for any vendors, cloud providers or other entities that connect to the firm’s network, including notification in the event of a breach.
- Conduct regular reviews of the security program and update as necessary.
Many law firms have multiple offices throughout the world, or attorneys who regularly travel to clients located in other countries. Silent Circle’s GoSilent enables law firms to lock down access to sensitive information, while still permitting safe access behind the firm’s firewall on an as-needed basis. As illustrated below, GoSilent secures a connection to the enterprise server and creates a secure “IPsec tunnel” inside the law firm’s firewall. Attorneys can then securely access sensitive client data without being exposed to attack over an open WiFi connection or open Internet. The GoSilent Server also securely communicates with IoT devices used by traveling attorneys or those working in a satellite office. Once GoSilent secures a connection to the enterprise server and creates a secure “IPsec tunnel” inside the law firm’s firewall, IP-enabled devices can then securely retrieve or send and store data behind the firm’s firewall.
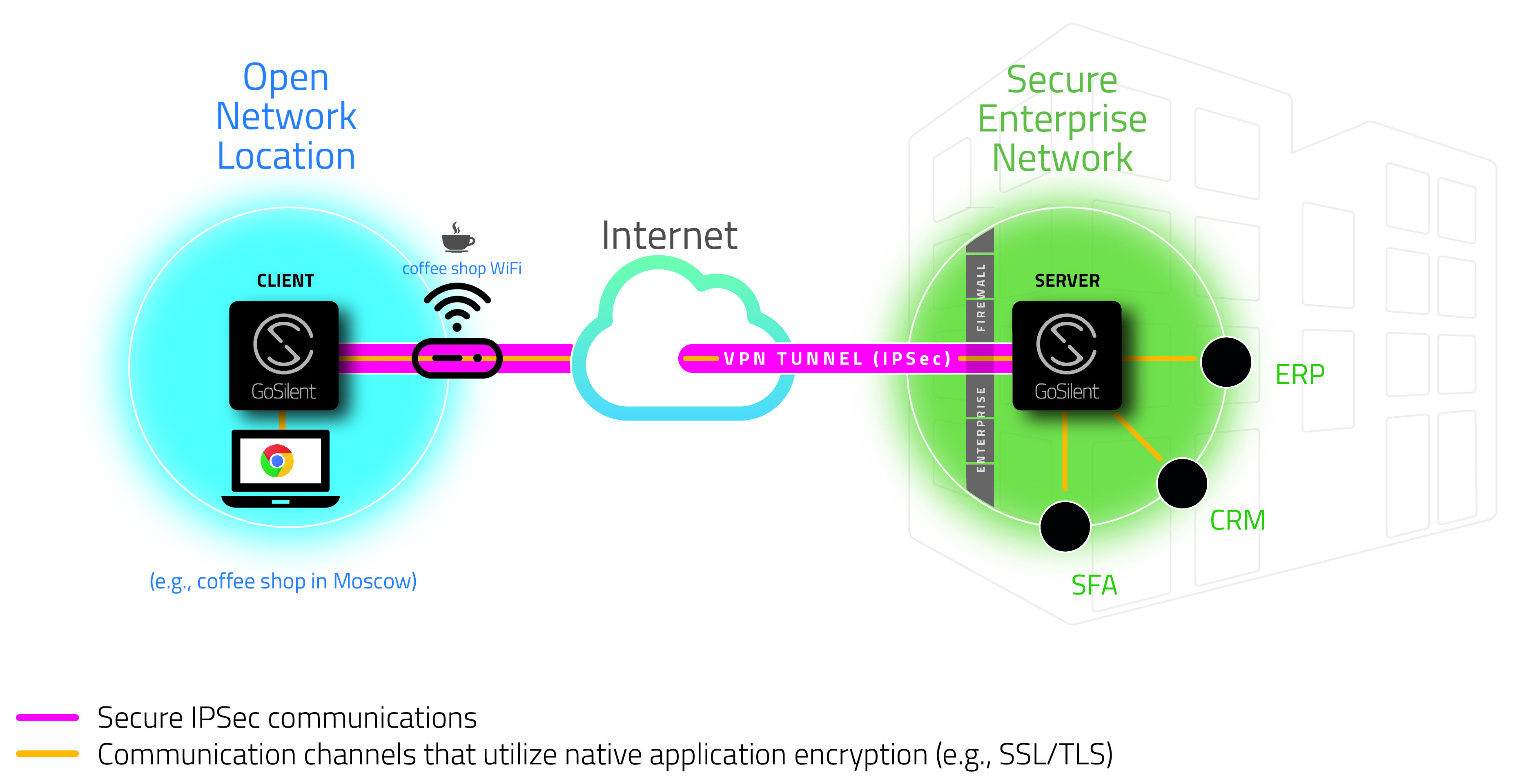
GoSilent safeguards from threats that target networks, data, and legal teams when operating external to a firm’s own networks and facilities. The mobile attorney can work securely using any device, from any location without data compromise, malware or device exploitation.